What should I do if I got a certificate error?
Part 1: For EAP and CPE web management interface
When try to visit the web interface via https in Chrome, such as the web interface of EAP/Omada Controller or Pharos CPE Series, it said server’s certificate is not trusted.
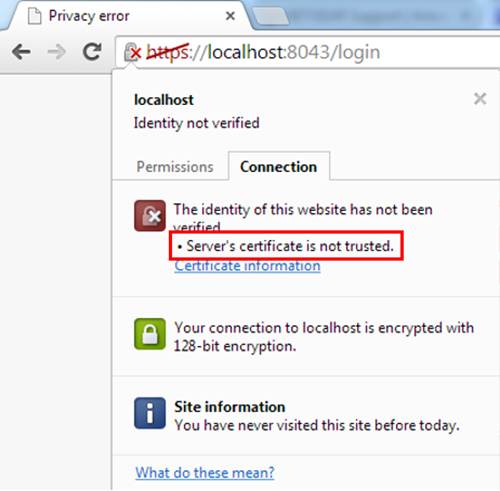
The certificate refers to how public websites trust each other. It is safe enough since we can make sure the IP address to be the same of the server’s.
Here are two examples for how to get through the certificate error when it occurred on TP-Link products.
1. Get through Certificate error on Chrome
Click on Advanced -- Proceed to localhost (unsafe), the web interface of EAP/Omada Controller will show up.


2. Get through Certificate error on Internet Explorer
While in Internet Explorer, you can just click on Continue to this website (not recommended) to visit the web interface.

Part 2: For EAP/Omada controller
For the EAP devices, its certificate can’t be changed; while for the EAP/Omada controller, you can manually import your own certificate if you have one.
Here are the instructions:
1. Disable the EAP/Omada controller on your computer.
2. Copy your keystore file (such as keystore.jks file) into the “keystore” folder of the EAP/Omada controller’s installation path.
3. Enter the “properties” folder of EAP/Omada controller installation path, edit the “jetty.properties” file.
4. Find the scripts below:
ssl.key.store.password=tplink
ssl.manager.password=tplink
ssl.trust.store.password=tplink
key.store.path=/keystore/eap.keystore
trust.store.path=/keystore/eap.keystore
5. Replace the scripts above with new scripts as below:
ssl.key.store.password= the storepass of your own certificate
ssl.manager.password= the keypass of your own certificate
ssl.trust.store.password= the storepass of your own certificate
key.store.path=/keystore/keystore.jks(your keystore file)
trust.store.path=/keystore/keystore.jks(your keystore file)
6. Launch the EAP controller, then you can use your domain name according to your certificate to visit the controller, such as https://hostname:8043, please note that the IP of hostname should be the IP of the controller PC.
¿Es útil este artículo?
Tus comentarios nos ayudan a mejorar esta web.







4.0-F_normal_1593323303811i.png)
4.0-F_normal_20221110005015k.png)