How to configure Shrew Soft VPN Client with TP-Link Router
Αυτό το άρθρο ισχύει για:
Take TL-ER6120 as an example.

To set up an IPsec VPV tunnel, you need to perform the following steps:
1. Make sure PCs can access to Internet;
2. Configuring IPsec VPN settings on TL-ER6120;
3. Configuring the Shrew VPN Client.
Configuring IPsec VPN on TL-ER6120
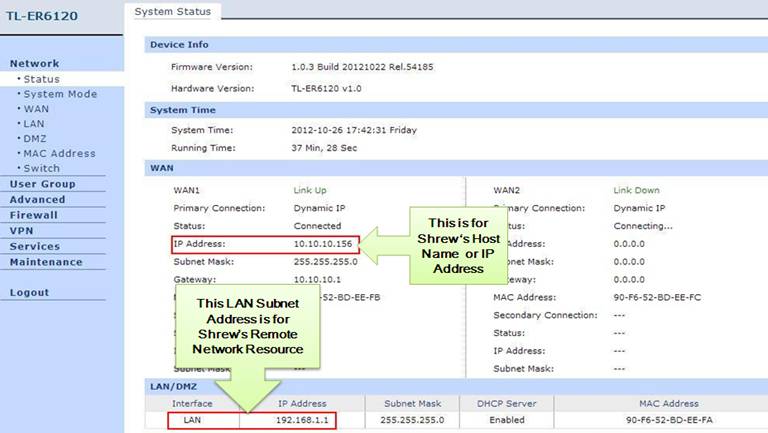
Step 1: Access the router’s management webpage; verify the settings needed on the router.
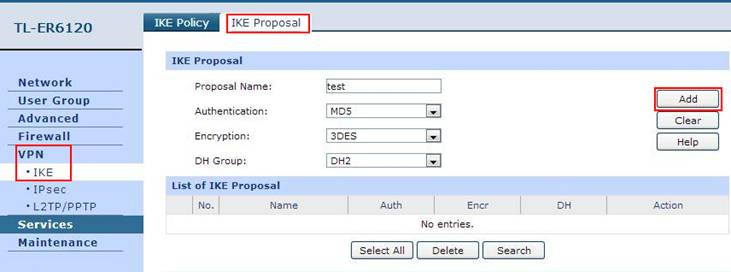
Step 2: On the management webpage, click on VPN then IKE Proposal. Under IKE Proposal, enter Proposal Name whatever you like, select Authentication, Encryption and DH Group, we use MD5, 3EDS,DH2 in this example. Click on Add.
Step 3: Click on IKE Policy, enter Policy Name whatever you like, we select Aggressive for Exchange Mode, select FQDN as ID Type and enter Local ID whatever you like, here we enter “123” for Local ID and “321” for Remote ID.
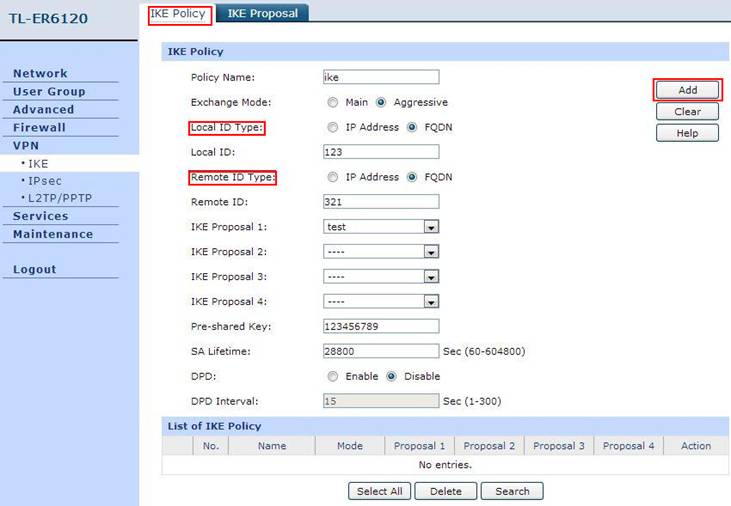
NOTE: We’d better select Aggressive for Exchange Mode. Once the client PC is behind a NAT device, we have to select FQDN as ID Type, otherwise, the VPN tunnel can’t be established.
Step 4: Under IKE Proposal 1, we select test in this example. Enter Pre-shared Key and SA Lifetime you want, DPD is disabled. Click on Add.
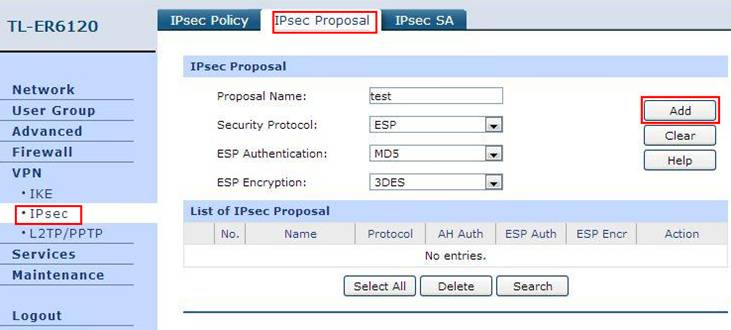
Step 5: Click on IPsec on the left menu, then IPsec Proposal. Select Security Protocol, ESP Authentication and ESP Encryption you want to enable on VPN tunnel. Here we use ESP, MD5 and 3DES for example. Click on Add.
Step 6: Click on IPsec Policy, enter Policy Name whatever you like, the Mode should be Client-to-LAN. Enter Local Subnet and select WAN port.
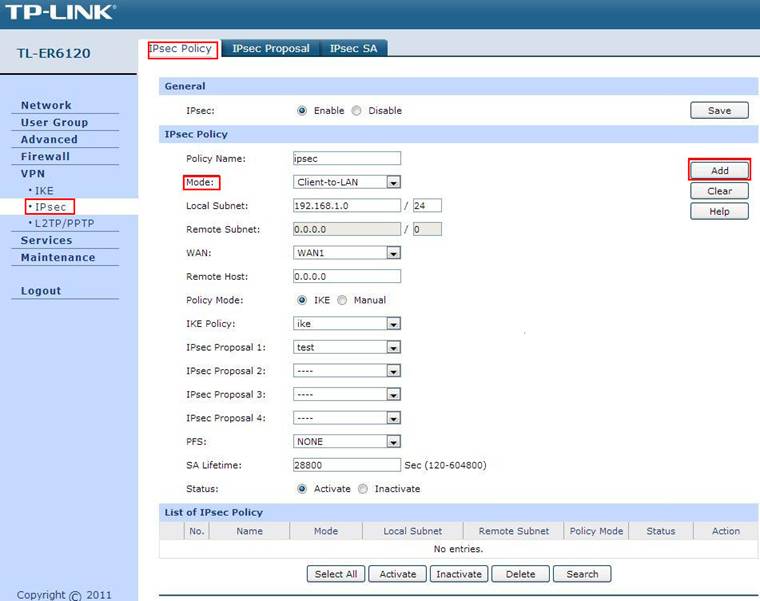
Step 7: Look for Policy Mode and select IKE. Under IKE Policy, we select ike which is used. Under IPsec Proposal, we use test in this example.
Step 8: Look for PFS, we set NONE here, under SA Lifetime, enter “28800” or the period you want. Look for Status then select Activate.
Step 9: Enable IPsec and then click on Add.
Configuring the Shrew VPN Client
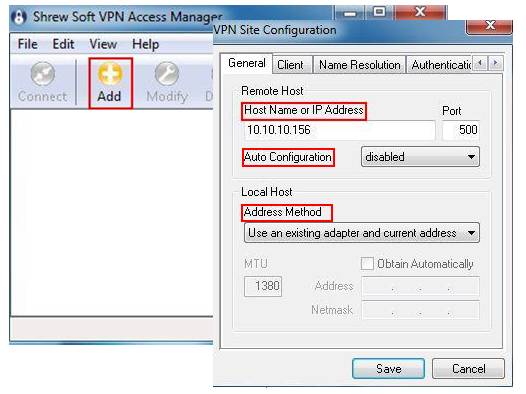
Step 1: Click on Add. Under Host Name or IP Address, enter the TL-ER6120’s WAN IP address, select disable for Auto Configuration. Under Address Method, we select Using an existing adapter and current address.
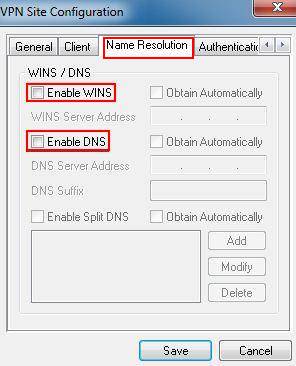
Step 2: Click on Name Resolution on the top menu, don’t tick the Enable WINS and Enable DNS.
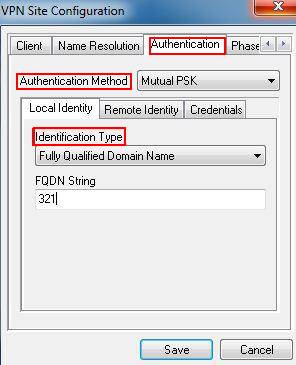
Step 3: Click on Authentication on the top menu, select Mutual PSK as Authentication. Under Identification Type, select Fully Qualified Domain Name and enter “321” for FQDN String.
Step 4: Click on Remote Identity, select Fully Qualified Domain Name as Identification Type and enter “123” for FQDN String.
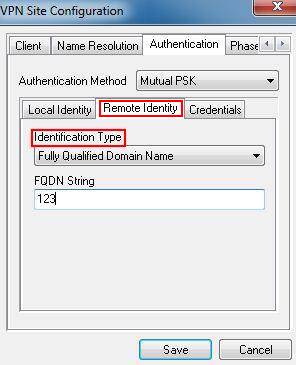
Step 5: Click on Credentials, the Pre Shared Key, should be the same as the Pre-shared Key on the TL-ER6120, it’s “123456789”.
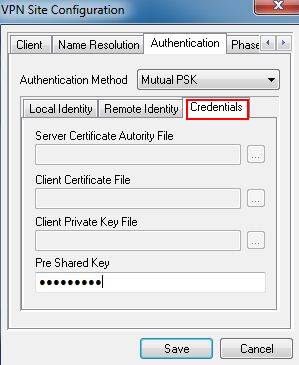
Step 6: Click on Phase 1, under the Proposal Parameters, the Exchange Type, DH Exchange, Cipher Algorithm, and Hash Algorithm are the same with TL-ER6120’s, we use aggressive, group 2, 3des,md5 here.
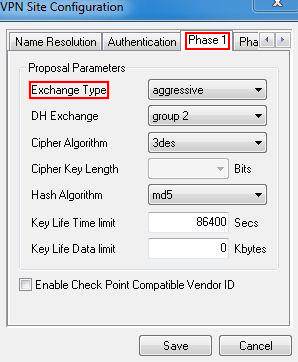
Step 7: Click on Phase 2, under the Proposal Parameters, the Transform Algorithm, HMAC Algorithm are the same with TL-ER6120’s we use esp-3des, md5 here. PFS Exchange and Compress Algorithm are disabled.
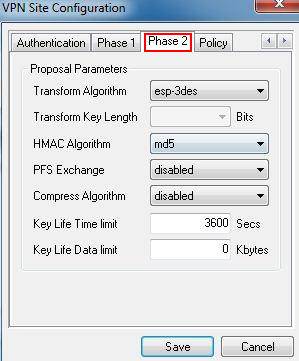
Step 8: Click on Policy, don’t tick Obtain Topology Automatically or Tunnel All. Then click on Add.
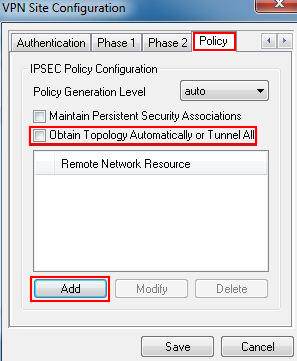
Step 9: Select Include as Type, enter the TL-ER6120’s LAN Subnet Address and Subnet Mask, it’s 192.168.1.0, 255.255.255.0. Then click on OK and Save.
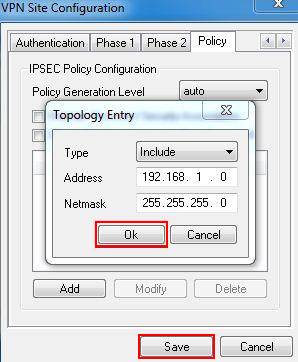
Step 10: Click on Connect.
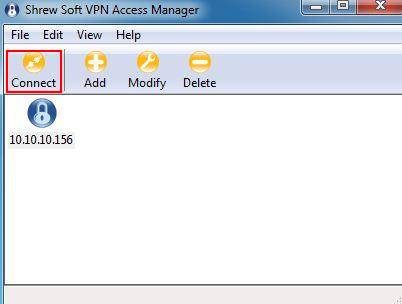
Step 11: Click on Connect.
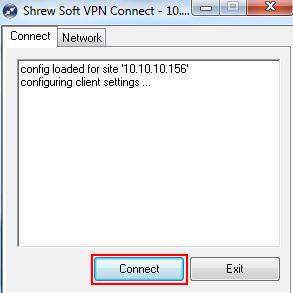
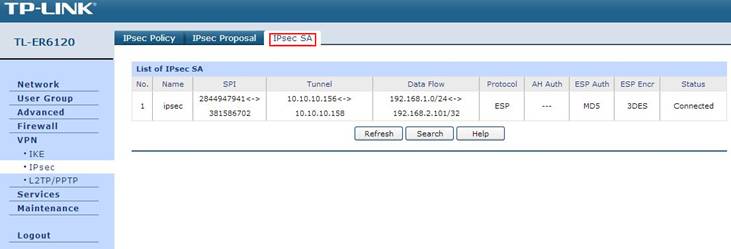
Step 12: If client connect to the VPN Server successfully, you can see IPsec SA on the list.
Είναι χρήσιμο αυτό το FAQ;
Τα σχόλιά σας συμβάλλουν στη βελτίωση αυτού του ιστότοπου.






