How to configure IGMP Snooping on Omada switches for hotel IPTV scenario
This article will introduce how to configure the IGMP Snooping on Omada switches in the hotel IPTV scenario, including the standalone mode and controller mode.
Note: All the CLI commands introduced in this article will only realize the basic features, and take only gigabit ethernet ports as example, for more detailed configuration and parameters, please check the CLI Guide.
1. Typical Topology
In the hotel IPTV scenario, typical topology as below:

Different from SOHO scenarios, most IPTV server or the IPTV multicast source is included in the hotel LAN network, so the multicast stream won’t be coming from WAN side. The IPTV source is usually connected to the core switch or an access switch then to the core switch so the multicast stream is able to hand out to all IPTV devices in LAN. Access switches are then connected to core switch and also connecting to the hotel TVs directly or via room APs.
2. How does the IGMP system works
The IGMP system consists of several parts: Multicast Source, IGMP Querier, IGMP Snooping, IGMP Receiver, check the figure below:

This figure shows a basic structure of the IGMP system, for our product, the device running IGMP Snooping is the switch, and our switch can also be configured as the IGMP Snooping Querier, to replace the querier in this figure.
In IGMP Snooping v2, there are three kinds of IGMP packets, the IGMP Query, IGMP Report and IGMP Leave. For the Multicast Source, if it doesn’t support the query feature, it will simply broadcast all the streams which is a waste of network resource, and enabling IGMP Snooping will handle this. The Querier will send IGMP Query, which consists of general query and specific query, here it’s usually general query, which will ask if there’s any device requesting for any multicast stream, and the IGMP Query will be forwarded by the switches and finally reaches the IGMP Receiver such as an IPTV, if someone want to watch a certain channel, the IPTV will send IGMP Report, which includes the information of this channel to request for this stream, which will also join this multicast group. When the user switch to another channel, which means the IPTV is no longer requesting this stream, it will send the IGMP Leave to leave this multicast group.
For all the devices running IGMP Snooping, there are two kinds of port roles to help creating multicast groups, the router port and the member port. For a switch, the port receiving the IGMP Query packet will become the router port, and the ports receiving IGMP Report/leave will become the member port. You can also assume that the router port is the port closest to the querier on a switch, and the member ports are the ports closest to receivers. So after the query process mentioned previously, the switch running IGMP Snooping will create multicast groups, including the multicast IP of this stream, the VLAN this stream is running in, and the ports participating in this group, including the router port and the member port. As mentioned before, the multicast source will simply broadcast the stream in the network, after the multicast groups created, the switch will only forward the corresponding multicast stream only to the router port and member ports, and the IGMP Report/Leave packets will only be forwarded from member port to the router port.
The basic working process of IGMP v2 is like this, and IGMP v3 has carried out some features to make the whole process more efficient, but the basic process and theory is the same as v2.
3. Overall Configuring Principles
Here we will introduce the overall configuring principles for IGMP Snooping, taking the previous topology as an example. These are some recommendations we made when configuring IGMP Snooping, which will help avoid misfunction and improve device efficiency, bringing a better user experience.
3.1 Disable IGMP featuers for router.
In hotel IPTV scenario, as the IPTV source is included in the LAN, so the multicast stream will not be entering from WAN side, and the router will actually not participate in the whole IGMP process. If you enable the IGMP feature on the router, then it will be recognized as a querier, so the switch port connecting to it will become a router port, and after that, a copy of all the multicast streams will be forwarded to the router, causing unnecessary load to the router, which may lead to high CPU and memory occupancy on router, affecting the normal function of router. That’s the reason why it’s recommended to disable the IGMP Query or IGMP Proxy feature on the router, no matter it’s TP-Link router or from other vendors.
3.2 Enable drop packets from unknown multicast groups.
When configuring IGMP Snooping, you can choose to forward or discard the packets of unknown groups. Here, we recommend you choose to discard all the packets from unknown groups, the reason is that for unknown groups, there isn’t a table recording the member ports, so actually the switch doesn’t know where these packets should be forwarded, and if you choose to forward them, they will be broadcasted, causing a waste of network resource, so the best choice is to discard them.
Note: for Omada switch, you have to enable both igmp snooping and mld snooping globally to enable multicast drop-unknown function.
3.3 IGMP Snooping Querier should be closest to source.
In hotel IPTV scenario, as the source needs report from end devices to determine which streams to be multicasted, an IGMP Snooping Querier is needed. There should be only one querier in the network and should be configured only on the switch closest to the IPTV source. Check the following figure for more intuitive explanation:

Here you can see, the Querier will send IGMP Query to others, which means it won’t receive any IGMP Query from others, so there isn’t a router port on the Querier, as we know that the switch with IGMP Snooping enabled will forward the IGMP Report to the router port, so in this scenario, this Querier will not forward the IGMP Report to anyone. The other switch won’t receive any IGMP Report, so no multicast group will be created, though the multicast source is keep sending the streams, all of them will be regarded as streams of unknown groups and got dropped because there isn’t any multicast group created on this switch. Set the switch cloeset to the multicast source as Querier will avoid this problem, the IGMP Snooping will be able to take affect through the whole network, save network resource while ensuring the multicast function normally.
3.4 Fast leave and report suppression should be closest to end device.
Fast leave will remove the port from IGMP group immediately when the switch receives the IGMP leave from end device, so the IPTV could switch to another channel faster, providing the users with a smooth experience, if not enabled, another specific query will be sent after receiving IGMP leave in order to determine if there are more IPTVs asking for this stream.
Report suppression will collect IGMP report for a same stream coming from different member ports and finally send out only one IGMP report through the router port, which will reduce the load for uplink, it’s recommended to enable report suppression in large multicasting networks, for example over three to four hundreds of IPTVs installed.
If you need to enable these two features, do remember to configure them on the access switch or the switch directly connecting the IPTVs. Check the figure below:

For fast leave, you need to ensure that there is only one IPTV connected to this port, so terminating the stream as soon as IGMP leave received will not affect other IPTVs watching the same channel. It’s not recommended to enable fast leave in the scenario shown in the figure when more than one IPTV is connected on one member port, enabling fast leave on this port will interrupt the stream for another TV still watching, it’s the same if you enable it on any higher level uplink switches, so remember to enable fast leave only on the access switch, and the ports connecting to only one IPTV.
For report suppression, enabling it on the access switch will save the most network resource for the whole network, the total number of IGMP Report packets will be lowered from the very beginning and save the bandwidth of uplinks, suppressing report on core switch but not access switch will be meaningless.
3.5 In case you have multiple IPTV sources in LAN.
Sometimes there are more than one IPTV sources in the network, it’s recommended you connect them to the same switch, and set this switch as IGMP Snooping Querier, this switch will also send general query to all the IPTV sources.
If your IPTV sources responde to the query, the switch will also establish IGMP groups for these IPTV sources, recording which port each stream is coming from, so the stream will not be forwarded to another IPTV source, causing heavy load or misfuntion on the source.
If your IPTV source do not respond to the IGMP query, you have two choices:
The first one is to configure configure port isolation and block the communication between the ports connected to each IPTV source.
Below are the configuration methods in standalone mode and controller mode.
- Configure port isolation in standalone mode:
Go to L2 FEATURES – Switching – Port – Port Isolation, here you will see a table, showing the ports and their forwarding list, the port will only be able to communicate with the ports included in the forwarding port list.

Click Edit on the upperright of the table to edit the forwarding list, for example, I want to cut the communication between port 1 and 2, just select port 1 and unselect port 2 for its forwarding port list, click Apply.

- Configure port isolation in controller mode:
In controller mode, go to Devices, click on the device connected with multiple IPTV Sources, click Manage Device to get into the device’s private configuration page, go to Ports, click the edit button of the ports connected with the IPTV Sources, tick Profile Overrides, then tick Port Isolation.
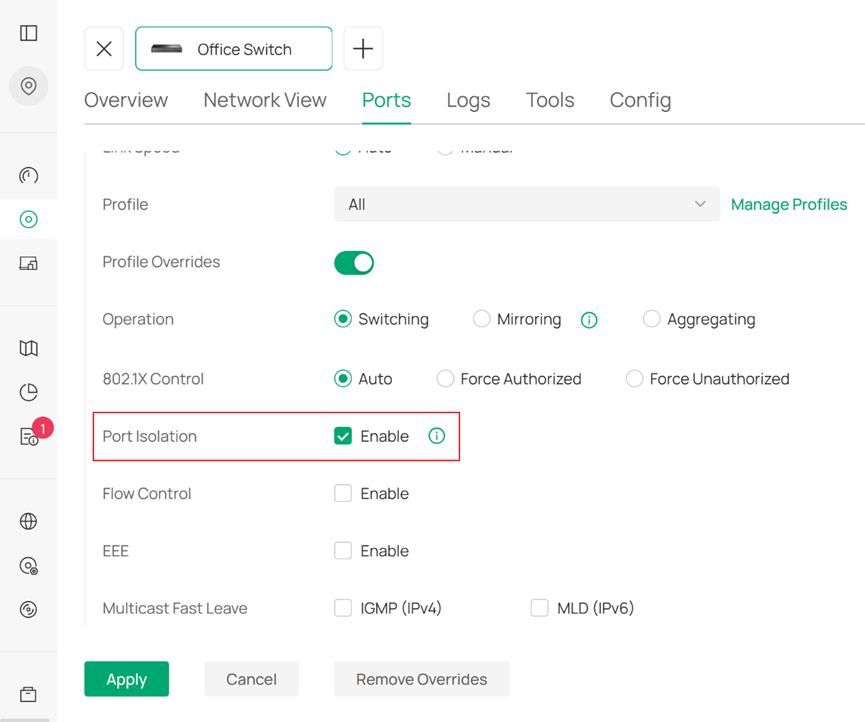
In controller mode, the communication between the ports with port isolation enabled will be cut, but kept the communication normal between the ports enabled and disabled port isolation.
Please note that when configuring profile override with this method, the profile override is enabled, which will override the configurations you made in the port profile, remember to make the necessary changes here.
The second one is to configure static IGMP group on the switch, manually create the groups and assign member ports to ensure the stream will not be forwarded from an IPTV source to another.
Below are the configuration methods in standalone mode and controller mode:
- Configure static multicast group in standalone mode:
Go to L2 FEATURES – Multicast – IGMP Snooping – Static Group Config, here is where you can configure the static multicast group in standalone mode, you will be able to manually bind the multicast IP, VLAN ID and the designated member ports.

When entering the static group config page, you will see the static multicast group table, click Add on the upper right of the table to start to configure a new static group, just input the corresponding multicast IP, the VLAN ID this multicast stream is running in, and select the member ports you want to add, in this scenario, just select the port connected to one of your IPTV Source and another port connected to the main network, for example, I have one of the IPTV Source connected to port 1 and the port 3 connected to core switch, so I just add port 1 and 3 into the static group. After configured, the multicast stream coming out of one IPTV Source will only be forwarded to the main network but not to any other IPTV Source.
- Configute static multicast group in controller mode:
In controller mode, port isoaltion needs to be configured through CLI template.
Go to Settings > CLI Configuration > Device CLI, click Create New Device CLI Profile, enter a name, description for it and then enter the CLI commands.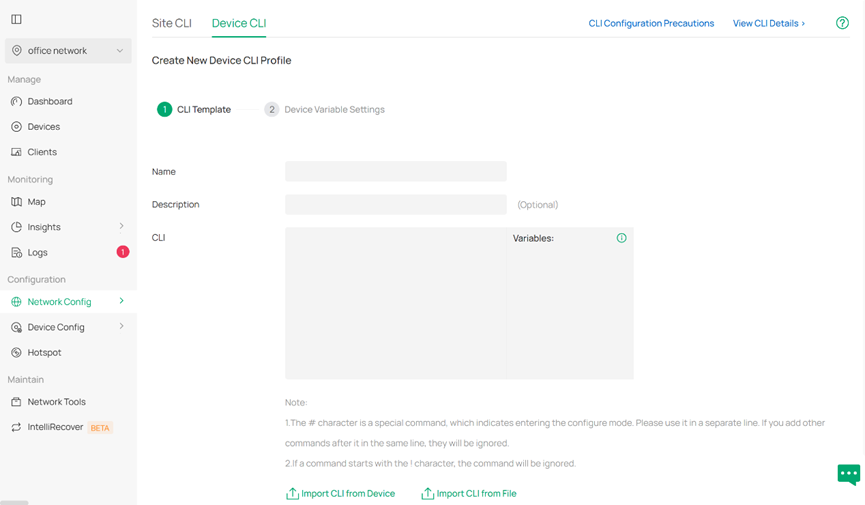
For example, one of my IPTV Source is connected to port 1, and port 3 is connected to the core switch, this IPTV Source is sending the stream with IP 235.0.0.1, running in VLAN 10, here is the command:
ip igmp snooping vlan-config 10 static 235.0.0.1 interface gigabitEthernet 1/0/1,1/0/3
As you have multiple multicast groups to be configured, you can enter all the commands here group by group. After finished entering the commands, click Next, and choose the device you want to apply the CLI.
Then click Confirm, then Save and you will see this CLI Template you have just created, click Apply to apply it on the chosen devices, you can also check if it has successfully applied by clicking View CLI Details on the upper-right corner.
4. Configuration under Standalone Mode
After entering the web GUI, you will find the IGMP related configurations in L2 FEATURES – Multicast – IGMP Snooping. You will find it divided into four parts: Global Config, Port Config, Static Group Config, IGMP Authentication. We will introduce the configuration for these parts.
4.1 Global Config.

This is the basic configuration page of IGMP Snooping, for the switches participating IGMP, you need to enable IGMP Snooping.
- IGMP Snooping: Ticking enable will enable it globally on the device.
- IGMP Version: The IGMP protocol is backward compatible, so you can simply choose v3, it will work well with other devices which support v1 or v2 only.
- Unknown Multicast Groups: It decides how will the switch process the stream with no IGMP group exsited, which means currently no one wants to watch it or it’s a stream sending to an unknown group. It’s recommended to set it as Discard in order to save network resource.
- Header Validation: Enabling it will check a few sums in the header, if the sums don’t match IGMP protocol, this packet will be dropped. We suggest not to enable it as some IPTV vendors may not closely follow the corresponding protocol, causing the packets created not able to pass the validation and got dropped, leading to misfunction of the whole system.
After finished configuring these four options, don’t forget to click Apply to apply it to the device.
For the IGMP VLAN Config, it will display all the VLANs created on the device, usually all the IPTV streams run in a dedicated VLAN, so please create a VLAN Interface for the IPTV stream first, then you will find this VLAN in the IGMP VLAN Config. You can click the edit button on the right of this VLAN and enter the VLAN config page.

- IGMP Snooping Status: Tick Enable to enable IGMP Snooping for VLAN.
- Fast Leave, Report Suppression: Decide whether to enable fast leave and report suppression on this device, please follow the principle from previous chapter.
- Member Port Aging Time, Router Port Aging Time, Leave time: Keep default or configure as you want.
- IGMP Snooping Querier: Please check the previous chapter about where you should enable the switch as an IGMP Snooping Querier. Tick Enable to set this switch as IGMP Snooping Querier and configure parameters including Query Interval, Maximum Response Time, Last Member Query Interval and Last Member Query Count, you can just keep it as default or set it manually as you like. For the General Query Source IP, it’s the IP address used to send the IGMP Query, ususally you should set it as the IP address of this switch, so it will be more convenient for you to check the packets sent from this querier.
- Static Router Ports, Forbidden Router Ports: No need to configure.
After finished configuring the IGMP VLAN configuration, click Save.
4.2 Port Config.
After configuring IGMP on this device globally and per VLAN, you also need to perform the port config, you can config it per port or LAG group. You need to config the IGMP Snooping and fast leave status for each port or LAG group.

Here you will see that for IGMP Snooping and Fast Leave, you can also choose to enable or disable them by port, by default, the IGMP Snooping is enabled on all ports, and Fast Leave is disabled on all ports. Explanation as below:
- IGMP Snooping: You can choose to enable or disable it globally, per VLAN and per port. To enable it on port A included in VLAN B, you must enable IGMP Snooping globally, in VLAN B and on port A, IGMP Snooping will take affect on a port only when the IGMP Snooping is enabled on all these three layers.
- Fast Leave: You can choose to enable or disable it per VLAN and per port and it will take affect with only one layer enabled. For example, port A and B is included in VLAN C. If you only enable it in VLAN C, even if you don’t enable it on port A and B, it will also take affect on them. If you enabled it on port A but not on port B and VLAN C, it will also take affect on port A.
4.3 Static Group Config.

In Static Group Config, you can click Add to configure and add static IGMP groups. To add a group, you need to configure the multicast IP address for this group and also the VLAN running this multicast group. Then choose the member ports you want to manually add into this static multicast group. After added, all the static multicast group including its VLAN ID and multicast IP, member ports will be displayed in the table.
4.4 IGMP Authentication.
Keep it by default.
5. Configuration under Controller Mode
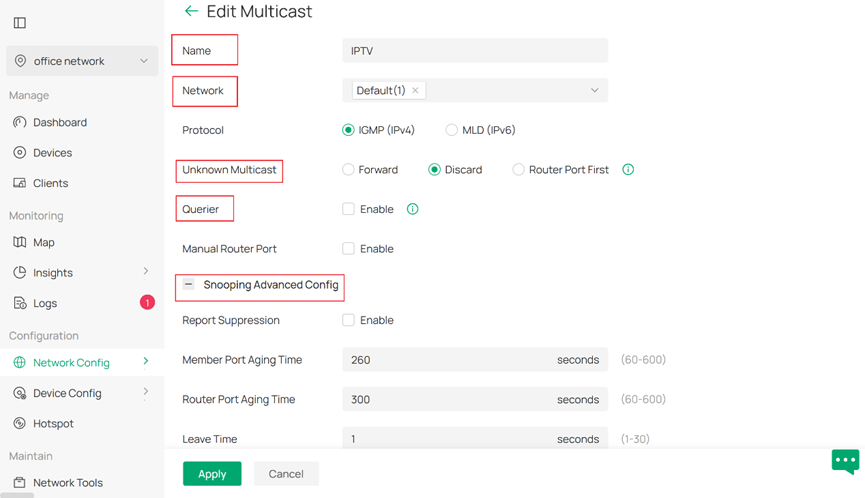
When using the devices in controller mode, go to Network Config > Network Settings > LAN > Multicast, click Add Multicast. In the following configuration page you will be able to configure the IGMP parameters as in standalone mode.
To start with, specify the Name of the multicast group configuration. Select the Network/VLAN for the multicast group. Then you will select how to deal with the stream with no IGMP group existing (aka Unknown Multicast). You can have detailed snooping parameters configured in Snooping Advanced Config.
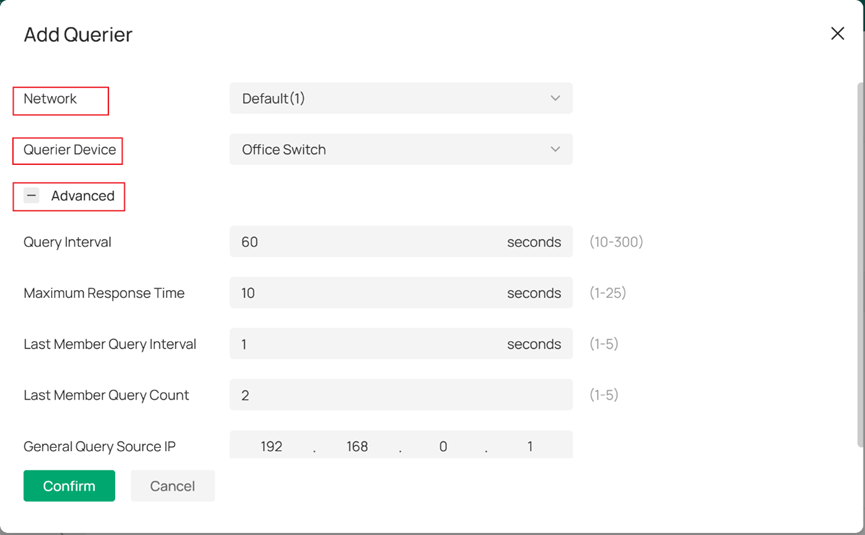
As for adding IGMP queriers for multicast group, first you need to enable Querier feature, then click Add on the right side to add queriers.
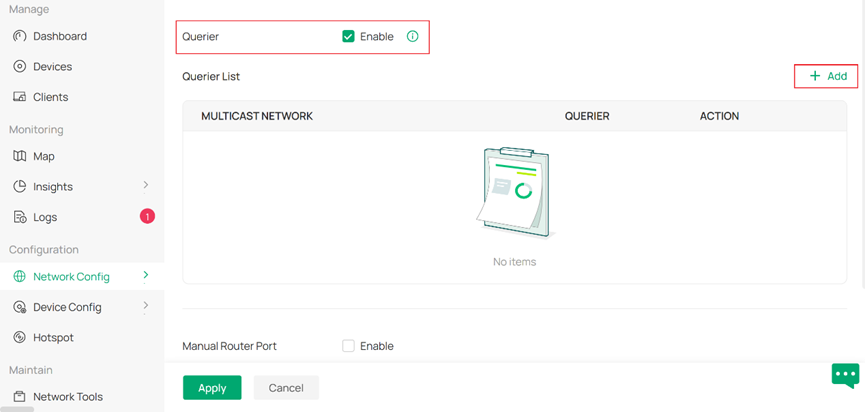
To add queriers, you need to specify the Network of the IGMP group and select a device to be the Querier Device. It is recommended to set the device nearest to the multicast source as the querier. Finally, you may configure any detailed querier configuration under the Advanced column.
Here we have finished introducing how to configure IGMP Snooping for typical hotel IPTV scenario on Omada L2+ and L3 switches under standalone mode or through Omada Controller.
Is this faq useful?
Your feedback helps improve this site.
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.










